WAF: The Unsung Hero of Web Application Security

Why Web Application Security Matters More Than Ever
A Web application firewall (WAF) is a security tool that filters, monitors, and blocks HTTP/HTTPS traffic between a web application and the internet. It protects your web applications from common attacks like SQL injection, cross-site scripting (XSS), and other threats that target the application layer.
Quick Definition:
- What it does: Acts as a shield between your web app and malicious traffic
- How it works: Inspects HTTP/HTTPS requests based on security rules
- What it blocks: SQL injection, XSS, bot attacks, zero-day exploits
- Where it sits: At Layer 7 of the OSI model (application layer)
- Why you need it: First line of defense against web-based attacks
Your web applications face constant threats. Every form submission, login page, and API call is a potential entry point for attackers. While network firewalls protect your broader infrastructure, they can’t see what’s happening inside your web traffic. That’s where a WAF comes in. Think of it as a trained guard who understands what suspicious behavior looks like at your front door.
The WAF market continues to grow as attacks on applications remain a leading cause of data breaches. Whether you’re running a small e-commerce site or managing enterprise applications, your web apps are under constant attack from automated bots and hackers.
The stakes are high. A single successful attack can mean:
- Stolen customer data
- Compliance violations and fines
- Downtime that costs thousands per hour
- Damaged reputation that takes years to rebuild
I’m Reade Taylor, and during my years as an engineer with IBM Internet Security Systems, I worked extensively with Web Application Firewall technologies to protect enterprise environments from application-layer attacks. At Cyber Command, we help businesses implement WAF solutions that provide real protection without the complexity.
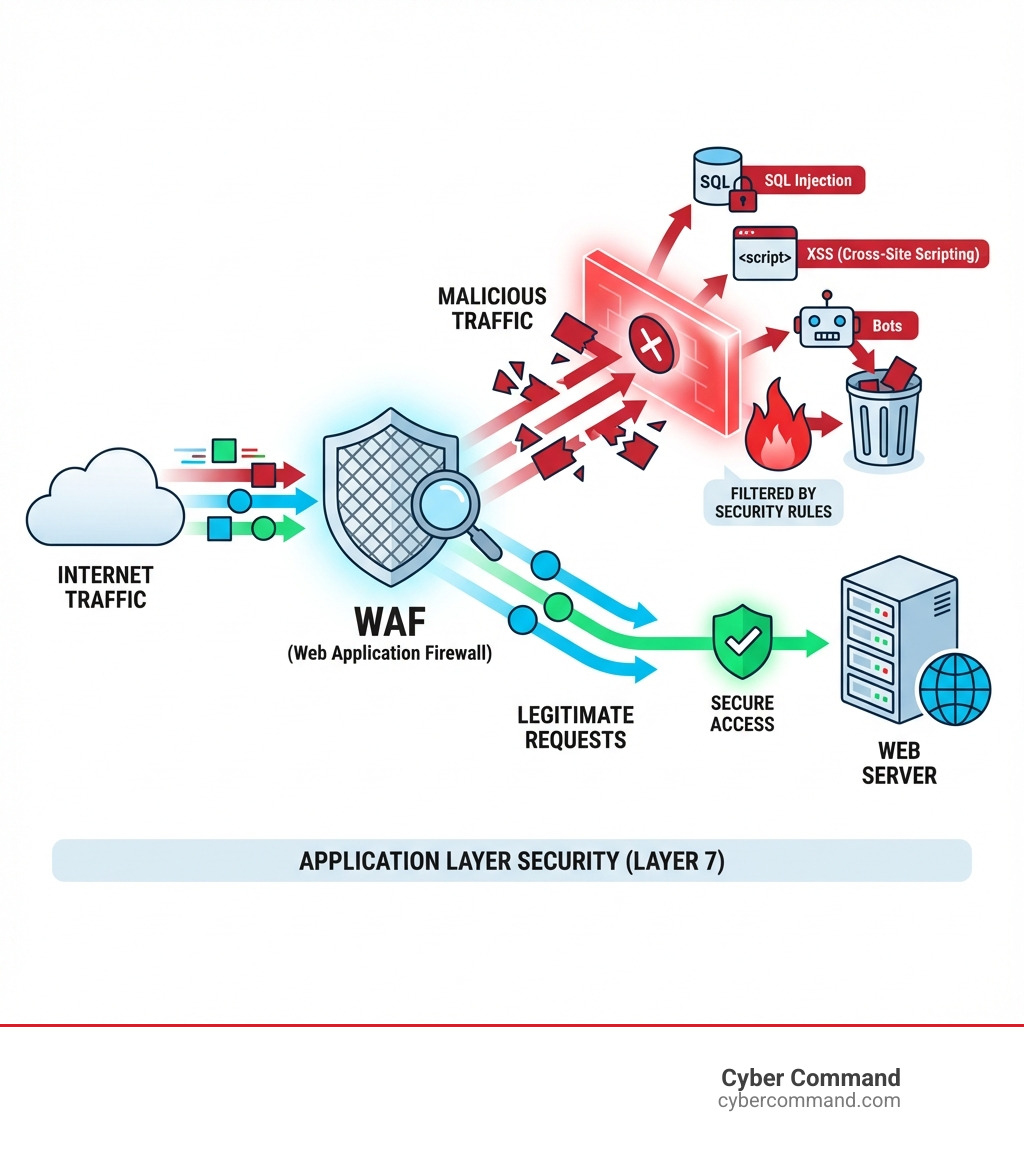
What is a Web Application Firewall?
A Web application firewall (WAF) is a specialized security system designed to protect web applications by filtering, monitoring, and blocking HTTP/S traffic between the web application and the Internet. Unlike traditional network firewalls, a WAF focuses specifically on the application layer (Layer 7 of the OSI model), where many common and complex cyber attacks occur.
Web applications are gateways to valuable data, making them prime targets for malicious actors. A WAF acts as a crucial first line of defense, creating a shield between your application and the internet. This dedicated protection helps mitigate a wide range of application layer attacks, such as cross-site scripting (XSS) and SQL injection. It’s a proactive measure that can significantly reduce the impact of cybersecurity threats on small business operations and prevent a cyber attack from compromising your digital assets.
How a WAF Protects Web Applications
A Web application firewall works by inspecting every HTTP/S request and response against a set of security policies. It acts like a highly vigilant bouncer, deciding which traffic is legitimate and which is malicious.
- Traffic Inspection: The WAF intercepts and analyzes all traffic to your web application, examining headers, body content, cookies, and URI parameters for patterns that indicate a potential attack.
- Policy Enforcement: The WAF enforces a security policy that defines “normal” traffic for your application. Any request that deviates from this policy or matches known attack signatures is flagged as suspicious.
- Blocking vs. Allowing Requests: Based on its analysis, the WAF can block malicious requests, allow legitimate requests, log suspicious activity, or challenge the request with a CAPTCHA to verify if the user is human.
- Virtual Patching: A key WAF capability is “virtual patching.” When a new vulnerability is found in your application, a custom WAF rule can be deployed to block attacks targeting that vulnerability. This provides an immediate, temporary fix, buying valuable time for developers to implement a permanent code-level solution. This is a critical component of proactive vulnerability assessment for threat management.
- Zero-Day Vulnerability Mitigation: By using custom attack signatures and behavioral analysis, a WAF can detect and block suspicious patterns even if the specific exploit is new, helping to mitigate “zero-day” vulnerabilities.
By acting as a reverse proxy, the WAF positions itself in front of your web application, ensuring that all incoming traffic passes through it first.
Key Benefits of Using a WAF
Implementing a Web application firewall offers a multitude of benefits that strengthen your overall security posture.
- Improved Security Posture: A WAF is a dedicated application-layer defense that catches threats traditional firewalls miss.
- Protection Against Common Exploits: WAFs are specifically designed to combat prevalent attacks such as SQL injection, cross-site scripting (XSS), and session hijacking.
- Compliance Assistance: Many regulatory standards, like the Payment Card Industry Data Security Standard (PCI DSS), recommend or require the use of a WAF to help your organization achieve and maintain compliance.
- Improved Application Performance: Many WAF solutions can also offer performance benefits like caching, which reduces response times and eases the load on your web servers.
- Bot Mitigation: WAFs include sophisticated bot management capabilities to differentiate between malicious bots (e.g., scrapers, credential stuffers) and legitimate ones (e.g., search engine crawlers).
- Reduced Downtime: By proactively blocking attacks, WAFs prevent successful breaches that could lead to application outages and sustained business operations.
- Data Protection: A WAF safeguards sensitive customer and company information handled by your web applications, preventing data exfiltration and ensuring data integrity.
These benefits contribute to a more robust and secure digital environment, aligning with our goals for comprehensive cybersecurity and managed services.
How WAFs Work: Deployment and Security Models
A Web application firewall operates at Layer 7, the application layer, of the OSI model. This is where web applications communicate via HTTP/S, allowing the WAF to inspect and filter traffic with a deep understanding of the application’s context.
A WAF acts as a type of reverse proxy, sitting in front of your web servers. This means all incoming traffic must pass through the WAF before reaching your application. This setup enables the WAF to analyze traffic based on carefully crafted WAF policies and security rules, providing a critical layer of defense for your network security for real estate and other industries.
WAF Deployment Models
The flexibility of Web application firewall solutions means they can be deployed in several ways, each with its own advantages and considerations. Choosing the right deployment model depends on your infrastructure, budget, and management preferences.
-
Network-Based WAFs:
- These are typically hardware-based appliances deployed within your network infrastructure.
- Pros: They offer high performance and minimal latency.
- Cons: They can be expensive to purchase and maintain, requiring physical installation and management.
-
Host-Based WAFs:
- These WAFs are integrated directly into the web application’s software or server.
- Pros: Generally less expensive than hardware WAFs and highly customizable.
- Cons: Consume server resources and can be complex to manage across multiple servers.
-
Cloud-Based WAFs (WAF-as-a-Service):
- A third-party provider hosts and manages the WAF service. Traffic is routed through the cloud WAF provider before reaching your application.
- Pros: Highly affordable, easy to implement, and continuously updated by the provider. This model significantly benefits organizations considering a cloud migration strategy.
- Cons: You hand over some control to a third party, and there might be potential latency concerns.
For many organizations, cloud-based WAFs offer an attractive balance of robust protection, ease of management, and cost-effectiveness.
Security Models: Blocklist vs. Allowlist
A Web application firewall employs different security models to identify and block malicious traffic. The two primary approaches are blocklist (negative security model) and allowlist (positive security model).
-
Blocklist (Negative Security Model):
- How it works: This model operates on the principle of “deny everything known to be bad.” The WAF maintains a list of known attack signatures and patterns. Any traffic that matches these predefined “bad” characteristics is blocked.
- Pros: Effective against known, common attacks. Relatively easy to implement initially.
- Cons: Can be bypassed by new, unknown attacks (zero-days). Requires constant updates.
-
Allowlist (Positive Security Model):
- How it works: This model is based on “allow only what is known to be good.” The WAF enforces a strict policy of what constitutes legitimate traffic. Only requests that perfectly match these pre-approved patterns are allowed through; everything else is blocked.
- Pros: Extremely secure against zero-day and sophisticated attacks.
- Cons: Can be complex to configure and has a higher risk of false positives (blocking legitimate traffic).
-
Hybrid Model:
- Most modern WAFs use a hybrid approach, combining the ease of a blocklist with the strong security of an allowlist. This offers robust and adaptable security.
Common Threats Mitigated and How a WAF Differs from Other Tools
A Web application firewall is engineered to combat a range of application-layer attacks that exploit vulnerabilities in your code or configuration.
Here are some of the primary attacks a WAF can mitigate:
- SQL Injection (SQLi): Prevents attackers from manipulating your database via malicious SQL code.
- Cross-Site Scripting (XSS): Blocks malicious scripts injected into websites that could be executed in users’ browsers.
- Broken Authentication: Exploits flaws in authentication or session management to compromise user accounts or gain unauthorized access.
- Sensitive Data Exposure: Attackers gain access to inadequately protected sensitive data, such as financial information, healthcare records, or personally identifiable information (PII).
- XML External Entities (XXE): Exploiting XML parsers to access local files, perform remote requests, or launch denial-of-service attacks.
- Broken Access Control: Attackers bypass authorization checks to access unauthorized functionality or data.
- Security Misconfigurations: Exploiting improperly configured servers, applications, or default credentials.
- Insecure Deserialization: Manipulating serialized objects to execute arbitrary code, conduct denial-of-service attacks, or bypass authentication.
- Cross-Site Request Forgery (CSRF): Tricking a logged-in user into executing unwanted actions on a web application.
- Malicious Bots and DDoS Attacks: Automated scripts designed for scraping, credential stuffing, spamming, or overwhelming an application with traffic (Layer 7 DDoS).
These attacks, particularly those on the OWASP Top 10 list, are the leading cause of data breaches. While a WAF cannot prevent every single type of cyber threat, such as some forms of ransomware prevention that target endpoints, it is exceptionally effective at protecting against application-specific vulnerabilities.
WAF and Other Security Tools: Complementary Roles
A Web application firewall is not a standalone security panacea. It’s a specialized tool that plays a vital role within a broader cybersecurity ecosystem. To achieve comprehensive protection, WAFs must work in conjunction with other security solutions.
Let’s clarify how a WAF differs from and complements other common security tools:
| Security Solution | OSI Layer Focus | Protection Focus | Typical Use Case |
|---|---|---|---|
| Web Application Firewall (WAF) | Layer 7 (Application) | Protects against web-based attacks like SQL injection, XSS, and CSRF by inspecting HTTP/S traffic. | Securing public-facing web applications and APIs from application-specific threats. |
| Network Firewall | Layers 3 & 4 (Network & Transport) | Filters traffic based on IP addresses, ports, and protocols. | Acts as a basic gatekeeper for the network, controlling access between network segments. |
| Next-Generation Firewall (NGFW) | Layers 3-7 | Combines traditional firewall features with intrusion prevention and application awareness. | Provides broad network security and visibility, but with less specialized web application protection than a WAF. |
| Intrusion Prevention System (IPS) | Layers 3-7 | Monitors network traffic for known malicious activity signatures and can block threats in real-time. | Detects and blocks a wide range of network-based threats, but lacks the deep application context of a WAF. |
The key difference is application-specific context. A WAF understands the language of web applications (HTTP/S) and can distinguish between legitimate and malicious requests with high accuracy. This makes it an indispensable part of a defense-in-depth strategy, working alongside tools like Next-Gen Firewalls to provide comprehensive protection.
Common Use Cases for WAFs
- Protecting Public-Facing Web Applications: Shielding corporate websites, customer portals, and SaaS platforms from a wide array of attacks.
- Securing APIs: Protecting APIs by inspecting incoming requests for malicious payloads and enforcing access control policies.
- E-commerce Protection: Preventing data breaches and helping maintain PCI DSS compliance for online stores that handle payment and personal data.
- Defending Login Pages: Mitigating brute-force and credential stuffing attacks on login pages through rate limiting and bot detection.
- Preventing Data Exfiltration: Monitoring outbound traffic to detect and block the exfiltration of sensitive data, helping you Secure Your Customers’ Data.
How WAFs Work: Deployment and Security Models
The effectiveness of a Web application firewall comes from its position at Layer 7 (the application layer) of the OSI model. This allows it to inspect the actual content of web traffic, not just where it’s coming from or going.
By acting as a reverse proxy in front of your web servers, a WAF analyzes all traffic against its security rules. This provides a critical defense for any web-based asset, from customer portals to internal applications, and is a key part of strategies like network security for real estate.
WAF Deployment Models
A Web application firewall can be deployed in several ways to fit your specific needs.
-
Network-Based WAFs:
- Description: Hardware appliances installed in your data center.
- Pros: High performance and low latency.
- Cons: High upfront cost and requires on-site management.
-
Host-Based WAFs:
- Description: Software integrated directly into the web server.
- Pros: Affordable and highly customizable.
- Cons: Uses server resources and can be complex to manage at scale.
-
Cloud-Based WAFs (WAF-as-a-Service):
- Description: A service where a third-party provider hosts and manages the WAF. Traffic is routed through the cloud WAF before reaching your application.
- Pros: Cost-effective, easy to implement, and always up-to-date. A great fit for businesses adopting a cloud migration strategy.
- Cons: Relies on a third-party provider.
Cloud-based WAFs are often the best choice for businesses in Florida and Texas, offering a balance of strong security, simple management, and predictable costs.
Security Models: Blocklist vs. Allowlist
A WAF’s core logic uses one of two models, or a hybrid of both, to filter traffic.
-
Blocklist (Negative Security Model):
- How it works: Blocks traffic that matches a list of known attack signatures. It’s like a bouncer with a list of known troublemakers.
- Pros: Simple to implement and effective against common threats.
- Cons: Ineffective against new or unknown (zero-day) attacks.
-
Allowlist (Positive Security Model):
- How it works: Only allows traffic that conforms to a strict definition of what is “good” or “normal.” Everything else is blocked. It’s like a bouncer with a strict guest list.
- Pros: Very secure against unknown threats.
- Cons: Can be complex to configure and may block legitimate traffic (false positives) if not tuned properly.
-
Hybrid Model:
- Most modern WAFs, including those we deploy, use a hybrid approach. They combine a blocklist for broad protection with an allowlist for critical application functions, offering robust and adaptable security.
Common Threats Mitigated and How a WAF Differs from Other Tools
A Web application firewall is a critical security control for protecting against a wide range of application-layer attacks that target vulnerabilities in your website’s code or configuration.
Here’s a list of the key threats a WAF is designed to mitigate, many of which are part of the OWASP Top 10 web application security risks:
- SQL Injection (SQLi): Prevents attackers from using malicious SQL code to access or corrupt your database.
- Cross-Site Scripting (XSS): Stops malicious scripts from being injected into your website and executed by other users.
- Broken Authentication: Helps secure login processes and session management to prevent account takeovers.
- Sensitive Data Exposure: Protects against attacks aimed at stealing sensitive information like credit card numbers or personal data.
- XML External Entities (XXE): Blocks attacks that exploit vulnerabilities in XML parsers.
- Broken Access Control: Enforces user permissions to prevent unauthorized access to data or functions.
- Security Misconfigurations: Provides a layer of protection against vulnerabilities caused by misconfigured servers or applications.
- Insecure Deserialization: Defends against attacks that manipulate serialized data to execute malicious code.
- Cross-Site Request Forgery (CSRF): Protects users from being tricked into performing unwanted actions on your site.
- Malicious Bots and DDoS Attacks: Identifies and blocks harmful automated traffic, including scrapers, credential stuffers, and application-layer DDoS attacks.
While a WAF is essential for web security, it should be part of a comprehensive strategy that includes other measures like ransomware prevention.
WAF and Other Security Tools: Complementary Roles
A Web application firewall is not a replacement for other security tools but a specialized component of a layered defense. Here’s how it compares to other common solutions:
| Security Solution | OSI Layer Focus | Protection Focus | Typical Use Case |
|---|---|---|---|
| Web Application Firewall (WAF) | Layer 7 (Application) | Protects against web-based attacks like SQL injection, XSS, and CSRF by inspecting HTTP/S traffic. | Securing public-facing web applications and APIs from application-specific threats. |
| Network Firewall | Layers 3 & 4 (Network & Transport) | Filters traffic based on IP addresses, ports, and protocols. | Acts as a basic gatekeeper for the network, controlling access between network segments. |
| Next-Generation Firewall (NGFW) | Layers 3-7 | Combines traditional firewall features with intrusion prevention and application awareness. | Provides broad network security and visibility, but with less specialized web application protection than a WAF. |
| Intrusion Prevention System (IPS) | Layers 3-7 | Monitors network traffic for known malicious activity signatures and can block threats in real-time. | Detects and blocks a wide range of network-based threats, but lacks the deep application context of a WAF. |
The key difference is application-specific context. A WAF understands the language of web applications (HTTP/S) and can distinguish between legitimate and malicious requests with high accuracy. This makes it an indispensable part of a defense-in-depth strategy, working alongside tools like Next-Gen Firewalls to provide comprehensive protection.
Common Use Cases for WAFs
- Protecting Public-Facing Web Applications: Shielding corporate websites, customer portals, and SaaS platforms from a wide array of attacks.
- Securing APIs: Protecting APIs by inspecting incoming requests for malicious payloads and enforcing access control policies.
- E-commerce Protection: Preventing data breaches and helping maintain PCI DSS compliance for online stores that handle payment and personal data.
- Defending Login Pages: Mitigating brute-force and credential stuffing attacks on login pages through rate limiting and bot detection.
- Preventing Data Exfiltration: Monitoring outbound traffic to detect and block the exfiltration of sensitive data, helping you Secure Your Customers’ Data.

