Cybersecurity

Today’s Reality
Cybersecurity Is No Longer Optional for Businesses
Today’s businesses face nonstop digital threats, and the old defenses firewalls, spam filters, and passwords are no longer enough. Modern attackers exploit every weakness, from human error to advanced malware, putting your data, revenue, and reputation at risk. Cybersecurity is now a must-have layer of protection that keeps your business resilient, secure, and ready for growth.
Human-Managed SOC: 24/7/365 Protection
Always-on, expert-led security that prevents, detects, and responds—fast.
Around-the-Clock Human Monitoring
Your security isn’t left to automation alone. Our analysts watch, hunt, and validate alerts—every hour of every day.
- Continuous log analysis
- Real-time threat hunting
- Human-led investigation & validation
Advanced Detection & Defense Tools
Layered technologies work together to identify, stop, and contain threats across your environment.
- SIEM (Security Information & Event Management)
- EDR (Endpoint Detection & Response)
- IDS/IPS (Intrusion Detection/Prevention)
- MDR (Managed Detection & Response)
Automated & Accelerated Response
We don’t just alert—you get action. Automation accelerates containment with humans steering critical decisions.
- SOAR (Security Orchestration, Automation & Response)
- Playbooks tailored to your environment
- Reduced false positives via human validation
Full Lifecycle Protection
Security across every stage of an attack to keep operations resilient and compliant.
- Prevent – NGAV, firewalls, zero-trust access
- Detect – SIEM, IDS/IPS, threat intel
- Respond – Investigation, containment, remediation
- Recover – Backups, reporting, continuity planning
Firewalls, spam filters, and passwords aren’t enough anymore—let’s prove it with data.

A Cyber Attack occurs every 39 Seconds, exposing organizations to continuous risk.
That’s roughly 2,200 attacks every single day, proving cybercriminals never rest. For businesses, it means the question isn’t if you’ll be targeted, but when. Without a strong cybersecurity strategy in place, even a single incident could disrupt operations, compromise sensitive data, and lead to major financial losses.
Top Cybersecurity Services to Protect Against Threats

Data Integrity & Confidentiality
Ensure that your data remains accurate, consistent, and protected from unauthorized access or tampering. Tools like threat detection, data backups, endpoint protection, and digital signatures help safeguard valuable information.
Authorization & Authentication
Strong access controls verify users, devices, and systems. Techniques include multi-factor authentication, biometrics, passwords, and permissions all designed to ensure only the right people have access.
Incident Response & Risk Management
Cybersecurity plans prepare businesses to detect, respond to, and recover from incidents quickly. Risk assessments, monitoring, and investigation practices minimize the impact of potential threats and help organizations stay resilient.
Strengthen National & Public Safety
Cybersecurity plays a vital role in safeguarding national data, critical infrastructure, and public services from hackers or malicious actors.
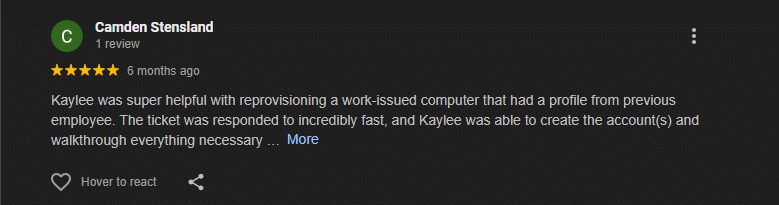
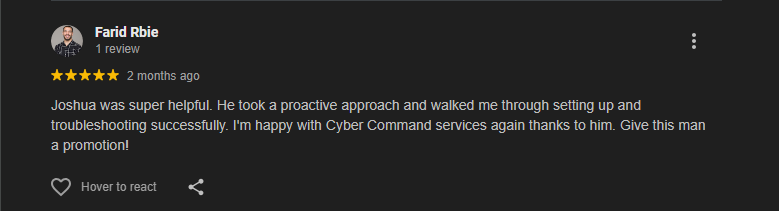
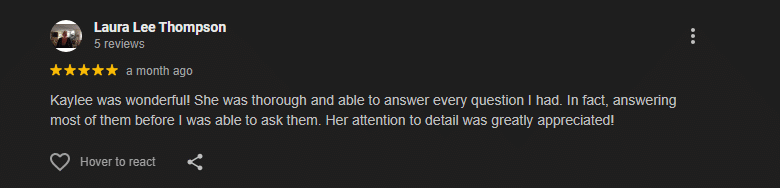
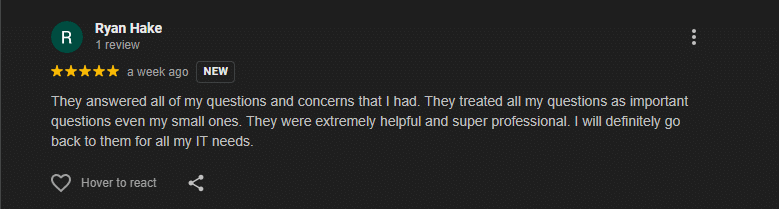
What Our Customers Say
Real Google reviews from our clients